Apple Defies FBI Orders to Unlock a Terrorist’s iPhone

The FBI has asked Apple to create a special version of its software that would remove one key security feature from its operating system. This backdoor would allow investigators unlimited password attempts, overriding the iPhone’s feature to wipe itself clean after 10 incorrect password attempts. It would allow investigators to unlock the phone through “brute force” methods.
Here’s where the case gets interesting: The FBI is only asking Apple to do this for one iPhone, which belongs to one of the San Bernardino shooters. Apple is fighting the order handed down by a U.S. federal magistrate judge, saying the implications this request carries go beyond fighting terrorism.
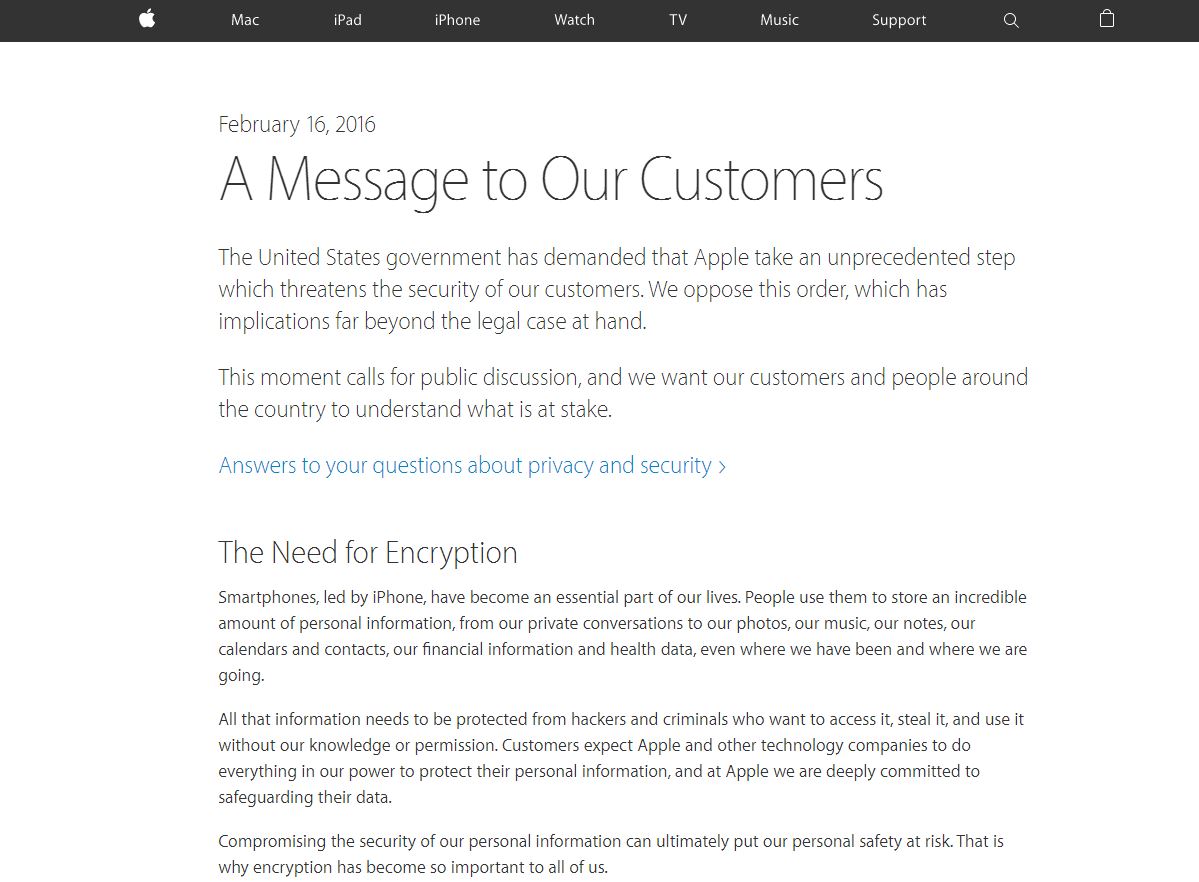
Apple CEO Tim Cook wrote an open letter titled A Message to Our Customersdetailing the company’s reasons for not complying with this order.
“Opposing this order is not something we take lightly,” Cook wrote. “We feel we must speak up in the face of what we see as an overreach by the U.S. government.”
“[T]he FBI wants us to make a new version of the iPhone operating system, circumventing several important security features, and install it on an iPhone recovered during the investigation,” Cook explained in the letter. “In the wrong hands, this software — which does not exist today — would have the potential to unlock any iPhone in someone’s physical possession.”
Apple has always stood firm in its belief that backdoors threaten consumer privacy and security. Cook believes allowing the equivalent of a “master key” to be made would then open a door that would be difficult to close.
“Once the information is known, or a way to bypass the code is revealed, the encryption can be defeated by anyone with that knowledge.”
This piece of software, some are calling FBiOS, would set a dangerous precedent.
“Rather than asking for legislative action through Congress, the FBI is proposing an unprecedented use of the All Writs Act of 1789 to justify an expansion of its authority.”
It’s important to think beyond the horror of the San Bernardino attack and to understand how asking to breach one phone could lead to a larger breach of privacy for citizens both innocent and guilty.
If the government knows it can use the All Writs Act to unlock one phone, it will be easier to access someone else’s phone or even create a surveillance network through iOS. Cook believes the FBI’s intentions are good, however, the broader implications of this order have too much potential for evil to be done.
The Electronic Frontier Foundation has announced its support of Apple’s decision to not code in a backdoor — no matter the reason. “Even if you trust the U.S. government, once this master key is created, governments around the world will surely demand that Apple undermine the security of their citizens as well.”
Rebecca MacKinnon, a founding member of the Global Network Initiative, says that “when governments are trying to use companies to control citizens, there are ways that companies can push back.”
***
Photo Credit: Andrew Burton/Getty Images
Natalie has been writing professionally for about 6 years. After graduating from Ithaca College with a degree in Feature Writing, she snagged a job at PCMag.com where she had the opportunity to review all the latest consumer gadgets. Since then she has become a writer for hire, freelancing for various websites. In her spare time, you may find her riding her motorcycle, reading YA novels, hiking, or playing video games. Follow her on Twitter: @nat_schumaker