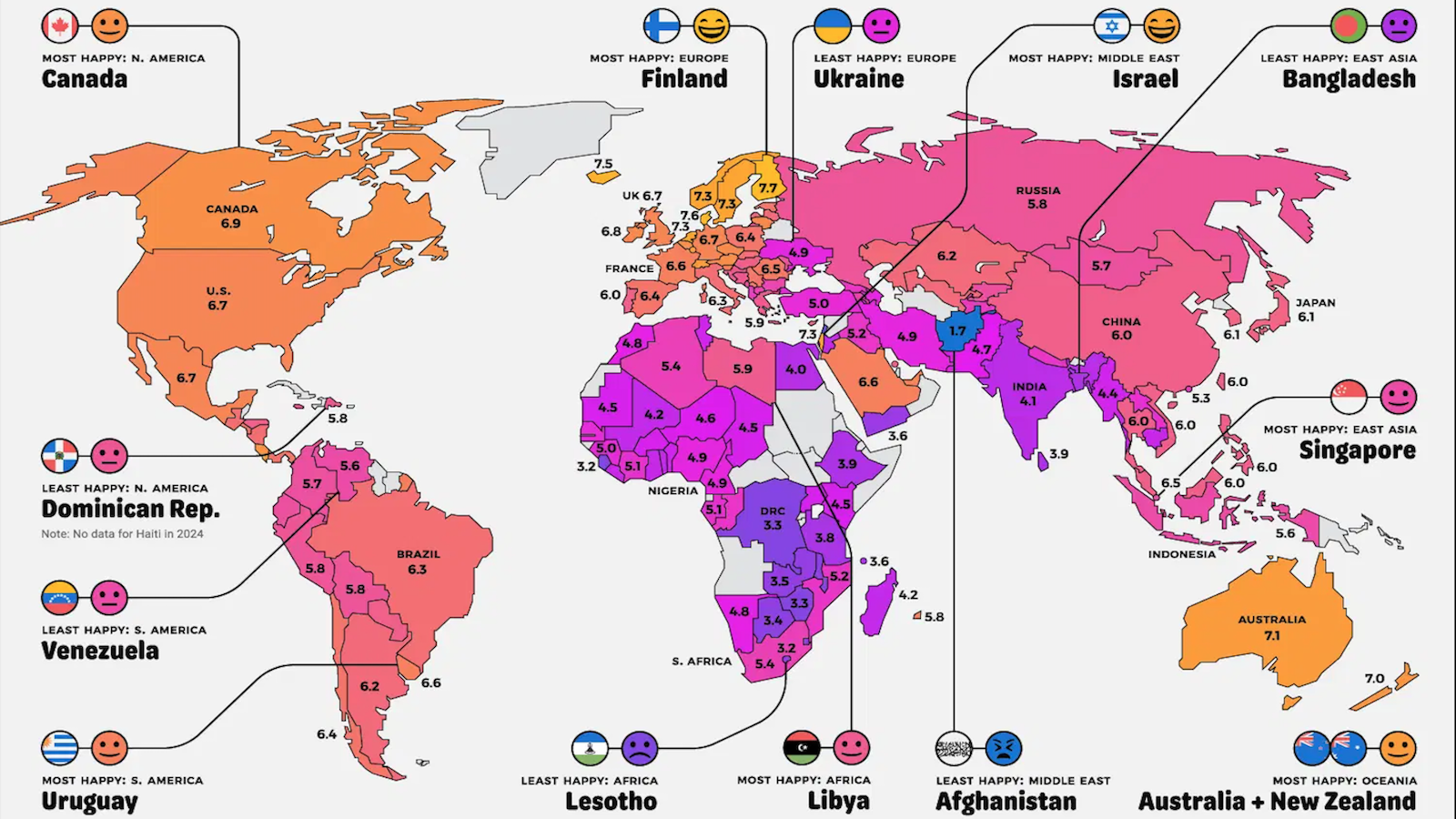
Cyber War Games: U.S. V. China

What’s the Big Idea?
In a revealing book about Chinese espionage called Tiger Trap: America’s Secret Spy War With China, intelligence expert David Wise details the long history of Chinese espionage going back to the Cold War. It is a different sort of spying that Americans are used to seeing.
“If a beach was an espionage target,” Wise notes, “the Russians would send in a sub, frogmen would steal ashore in the dark of night and with great secrecy collect several buckets of sand and take them back to Moscow.“
On the other hand, the US “would target the beach with satellites and produce reams of data.“
The Chinese, however, would send in a thousand tourists, each assigned to collect a single grain of sand. When they returned, they would be asked to shake out their towels. And they would end up knowing more about the sand than anyone else.”
In other words, China has been co-opting the thousands of students, tourists, business travelers and scientists who visit the US each year. Wise argues they are probably also at least giving tacit permission to hackers to attack the computers of companies and governments in the US, Taiwan, India, and other nations. Like the U.S., China has devised war games to disrupt the digital networks of an adversary in a war. While the Chinese government has steadfastly denied this, the available evidence points to the contrary. For instance, a Wikileaks cable revealed that the Chinese Government coordinated intrusions in Google’s systems in 2010.
The U.S. government has not made much a fuss about all of this, according to Wise, because China effectively is the bank that holds the mortgage to our “house.”
What’s the Significance?
Cyber warfare involves more than just reading people’s emails. Wise sites security experts who worry about the compromise of not only software but hardware such as missiles, aircraft, and radar systems:
“One reason is that only about 2 percent of the integrated circuits purchased every year by the military are manufactured in the United States. And even most American chip makers have moved offshore, where labor is cheaper. A computer chip made with a hidden, malicious flaw could sabotage a weapons system. And the compromised hardware is almost impossible to detect.”
In fact, Wise writes that a chip might be embedded with a so-called “kill switch” that would allow a weapon to be disabled by remote control. This may seem far-fetched, but there are unconfirmed reports that Israeli intelligence may have used such a “kill switch” to shut down Syrian air defenses during an attack in 2007.
Wise convincingly demonstrates how “a few key strokes on the computer” can function as a weapon of mass destruction. CIA director James Woolsey tells him: “Taking down the grid for months comes as close to a nuclear attack with many weapons on the United States as anything could. You’d have mass starvation and death from thirst and all the rest.”
In his interview with Big Think, Wise describes the digital war games that are being played out by the U.S. and China, and where the U.S. might be the most vulnerable to attack. Watch here: